
Do you want to apply secure certificates to multiple websites on the same web server? You want them to renew automatically? And want them to be free! Then read on.
A few years back, one of my colleagues put me onto this process and I’ve been using it ever since and now I’ve documented it here.
I look after a few Linux web servers on AWS and GCP. The administration overhead around purchasing new certificates, setting them up, renewing is time-consuming. It also costs money, although we always went for the budget secure certificates. That’s because all of the websites that we look after on these servers are informational rather than transactional.
Free secure certificates with Certbot
When I passed over the administration of the process to a colleague, he found a better way. That was to use Let’s Encrypt’s Certbot,. They give you a free 90 day secure certificate and a process to automatically renew it before it expires. The certificates go through a similar process to the domain authentication via DNS as the budget certificates but that is verified automatically too. If you need to have insurance with your secured certificate in case your site becomes compromised then you’ll need to look at paid options.
The guy who set this up on one of our servers then moved on and the servers came back to me. After I had added a few domains as their paid for certificate expired, I then added Certbot and the auto-renew process to other servers.
If you already have a site to play with then use that and skip the first section on setting up a test site. All of the following screenshots are from a free Ubuntu 18.04 LTS server that I have on AWS. I have run Certbot on three LTS versions of Ubuntu 14.04, 16.04 and 18.04. I don’t remember there being any difference.
Setting up a test site
You can skip this if you already have a test site. Otherwise continue on. First you will need a domain name and I purchased “trysite.net” for playing around like this and so I’ll use that. After setting up my Ubuntu server, I pointed the DNS entries to that IP address (I made sure it was a static IP address on AWS so if it gets rebooted, I don’t lose the IP address). So let’s assume that the domain has the correct DNS entry and you’ve waited a sufficient amount of time (2 hours should do) so that it has propagated locally at least.
From the command line interface, create a directory for the new site, chnage the owner from root to www-data and then copy a suitable HTML file for the test. I’ve used a simple Nothing to see here message, which I have as the default for the server. I just copied that and modified it slightly.
sudo mkdir /var/www/trysite/
sudo chown www-data:www-data /var/www/trysite/
sudo cp /var/www/html/index.html /var/www/trysite/
sudo nano /var/www/trysite/index.html
Then taking a copy of the default site configurations, I have modified them with the details of the test site.
sudo cp /etc/apache2/sites-available/000-default.conf /etc/apache2/sites-available/000-trysite.conf
sudo cp /etc/apache2/sites-available/default-ssl.conf /etc/apache2/sites-available/trysite-ssl.conf
sudo nano /etc/apache2/sites-available/000-trysite.conf
sudo nano /etc/apache2/sites-available/trysite-ssl.conf
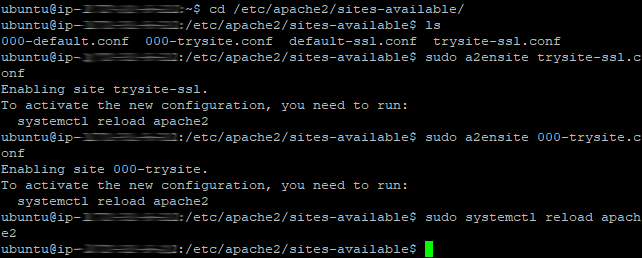
Change the directory to the sites available in Apache, enable both configurations for port 80 and 443 and then reload the configurations in Apache.
cd /etc/apache2/sites-available/
sudo a2ensite 000-trysite.conf
sudo a2ensite trysite-ssl.conf
sudo systemctl reload apache2
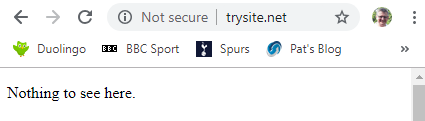
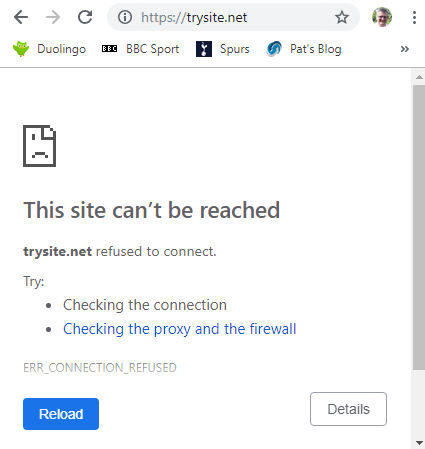
Test the HTTP and HTTPS versions in the browser to make sure HTTP returns the page (I edited so that it wasn’t exactly the same as my default for the server) and that HTTPS causes an error.
Step-by-step Certbot install
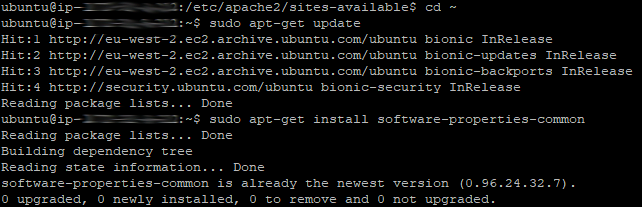
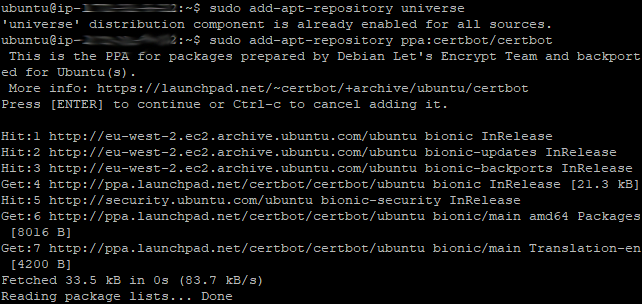
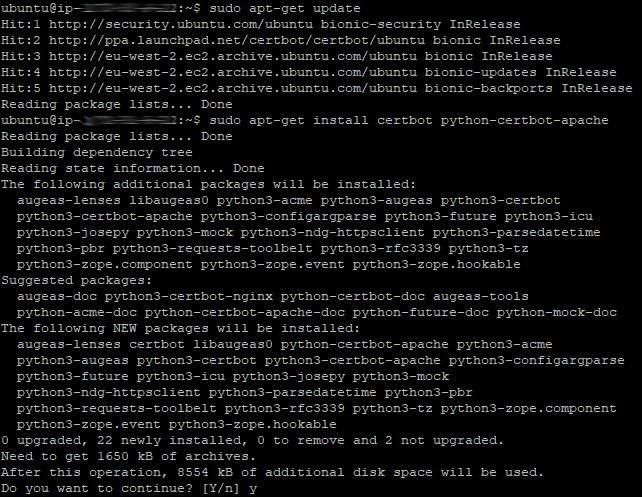
First we get an update, install common properties, add a couple of repositories, run another update and then install Certbot and Certbot for Apache.
The following six commands will install Certbot. I’ve used apt-get rather than apt so the same commands will apply to all versions of Ununtu. If you are not running Ubuntu, the commands may be slightly different. The screenshots show the typical actions performed by each command too.
sudo apt-get update
sudo apt-get install software-properties-common
sudo add-apt-repository universe
sudo add-apt-repository ppa:certbot/certbot
sudo apt-get update
sudo apt-get install certbot python-certbot-apache
Installing Certbot certificates
After Certbot is installed, it is time to add a secure certificate to a site. There are two ways to do this;
1. Run Certbot for apache without a domain specified so you can select one or more domains from a list. Command below.
sudo certbot ââapache
2. Run Certbot for apache with a domain (or domains) specified using -d before each domain name. Command example below.
sudo certbot ââapache -d trysite.net -d www.trysite.net
I’ll just pick from a list using the first method as it’s less typing. If you have domain aliases set up then you’ll need to select those too. On this server, I only set the domain name as trysite.net and didn’t set a www alias so I will only select a single domain. If you want to select multiple domains separate the domain number with a comma.
So after running the “certbot –apache” command, you will be prompted for an email address and to accept the terms of service. Once you do, you will be prompted with a list of available domain names on your server, including any aliases. Select the number (or numbers separated by commas) for the domain(s) you wish to apply a secure certificate to. It will replace a previously installed certificate.
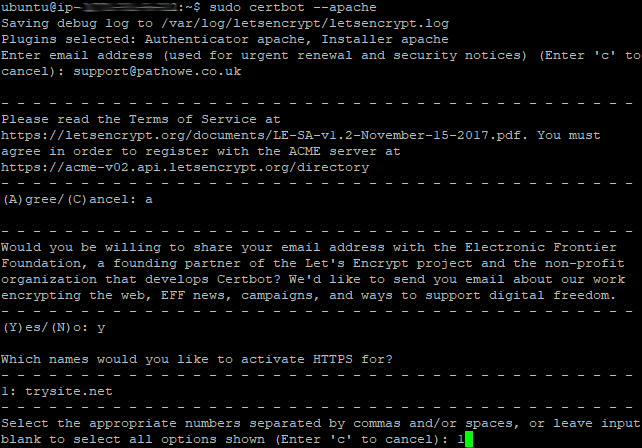
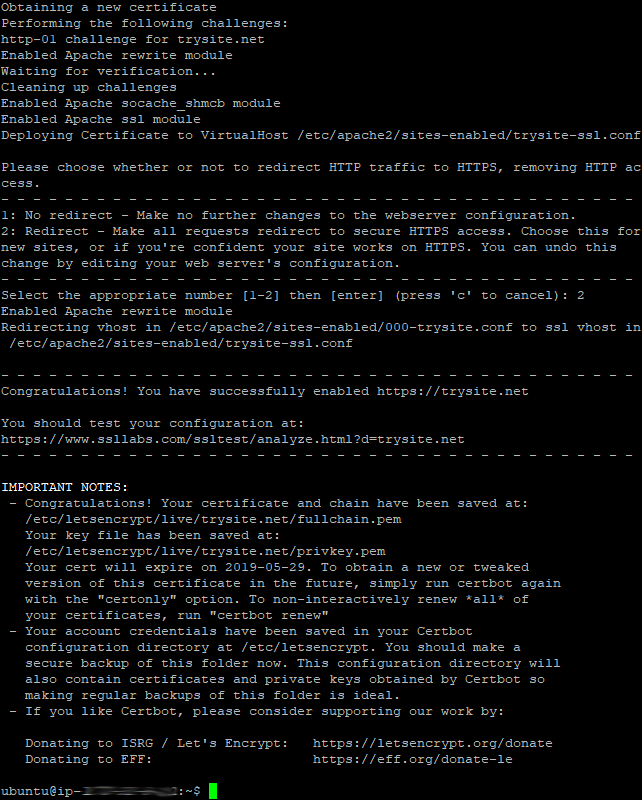
The final step is whether you want Certbot to modify your site configuration file for automatic redirection.
Select 1 if you do not want this (i.e. you want to run both port 80 and 443) or you have already set it to automatically redirect.
OR
Select 2 if you want Certbot to sort that out for you.
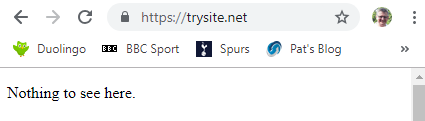
Now visit the site in your browser using HTTPS to check that it works.
Testing automatic certificate renewal
By default the Certbot installation added a Cron job (scheduled task) to your server to check for any certificates that are coming up to their expiry date and to renew them automatically so you never have to worry about keeping track of them again.
If you want to test this is working you can run a simulation of the renewal process that takes place automatically in the Cron job.
sudo certbot renew ââdry-run
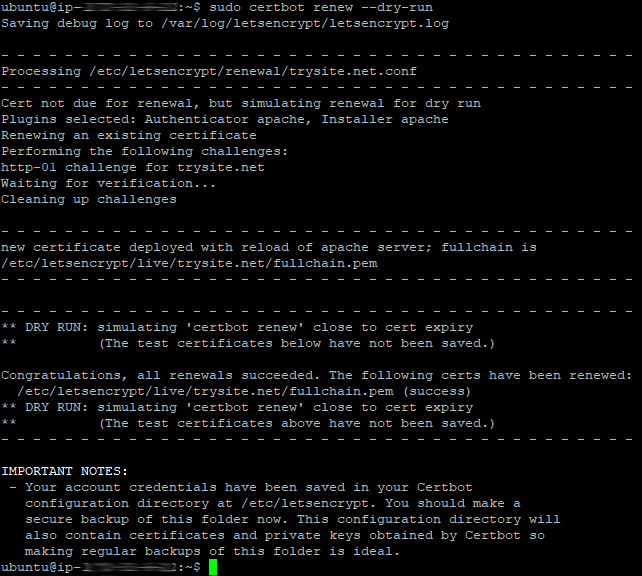
If you ever need to run the secure certificate renewals manually, then use the same command without the dry run flag.
Finally
Certbot is run by a non-profit and if you are utilising their free services you should donate something to help keep them going. You can do so on their official site, where you can also find instructions for other installations, including wildcard certificates. https://supporters.eff.org/donate/support-work-on-certbot
