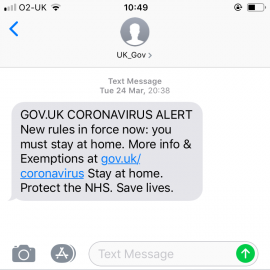
It might be April Fools Day but this short article on protecting yourself from scammers is not a prank and for the thousands of people who get scammed every day it is no laughing matter. If there is one group of people who relish a crisis, it’s the scammers. These criminals are looking to exploit the most vulnerable when they need help the most. They don’t see it as a crime. They see vulnerability as weakness that they can and should exploit. It is human nature to trust others until
Setting up and testing free secure certificates

Do you want to apply secure certificates to multiple websites on the same web server? You want them to renew automatically? And want them to be free! Then read on. A few years back, one of my colleagues put me onto this process and I’ve been using it ever since and now I’ve documented it here. I look after a few Linux web servers on AWS and GCP. The administration overhead around purchasing new certificates, setting them up, renewing is time-consuming. It also costs money, although we always went for
Six steps to staying safe online and securing your devices

After all the stories about the latest malware attacks, I wanted to post a collection of tips that should help you and others on your network (home or work) with six steps to staying safe online and securing your devices against malicious threats. It’s quite simple really and if you follow these rules then you won’t become a victim. 1. Patching Keep your operating system and software patched to the highest level and do so as soon as you can after the patch has been released. If your operating system
Steps to securing your Apache web server on Ubuntu

This article goes through some of the things you can do to protect your web server from certain types of attacks and to keep the disclosure of information down to a minimum. It will show you how to help prevent clickjacking, SSL cipher or mime-based attacks. It will show you how to avoid error messages and other methods giving away more information than is needed. These can mostly be prevented at a server level so that they apply to all websites that you publish on the server. A brief description
Advice to help avoid becoming an email scam victim

During 2014, I wrote several times about scam emails and that advice still applies today at the start of 2016. Scammers are finding new ways to con you each day but they also keep trying the old ways too as people are still falling for it. In this short article I reiterate that advice in the three main areas of email scams covering attachments, links and cons. In brief the way you can stay safe from nearly all of scams is to never click on any links and never open
Final update on email scams in 2014

I have decided today to close off the special report on email scams in 2014. It has been going for nearly 6 months and most of the scam emails I receive have already been captured on that page. It is time to now switch on my anti-spam software and junk mail filter at the mail server so that I won’t get so many in my mailbox. I created the report to catalogue the different ways that scammers try to catch you out either to click a link to a dodgy
Taking action against unwanted telephone callers

I gets lots of spam/phishing emails but also an increasing number of unsolicited telephone calls until I took some action. These calls range from legitimate companies cold calling to illegitimate scammers trying to trick me into divulging information or buying something that I don’t need. Basically, I have never bought anything from anyone that has cold called me. Even if I took a call and was interested in, “double glazing”, “home security” or whatever else they are selling, I will always make a point to never buy from a cold
An update on email scams with recent examples
During the last couple of months, I’ve been collecting all the scam emails that I’ve been receiving and publishing them on a separate page. Just recently scam email activity has risen quite steeply so I thought I would give a short reminder here about my “Special report showing examples of email scams in 2014” page. The page was getting quite long as I was just listing them as they came in so they were in order of the date received with the newest at the top. I didn’t want to
What you need to know about the heartbleed bug

You will no doubt have heard about the Heartbleed bug and here I’ll give you a quick idea of what it is and any action you need to take. For full details you can visit the Heartbleed website. So what is it? Heartbleed affects secure websites and other secure communication channels but for simplicity I’ll describe what happens on a website. Normally, you visit a website via HTTP (hypertext transfer protocol) and the traffic is not encrypted so anyone that interrupts that communication can see the data transferred. Websites that
Stop the scammers by raising awareness with email scam examples

I get a lot of phishing emails and I would like to make everyone aware of them whenever they arrive. However, it’s impractical to make a posting every day that I receive them as that is every single day so I thought I would introduce a new page where I can keep adding the new email scams. I can’t actually remember a day when at least one scam comes through my various mailboxes but I’ll only show them the first time they hit my mailbox (it would be a very